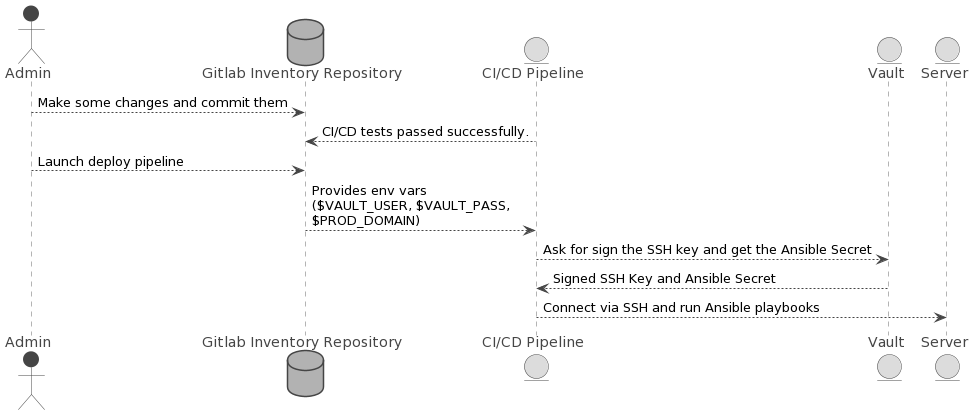
¶ How Gitlab CI/CD deploys works
¶ Setup process
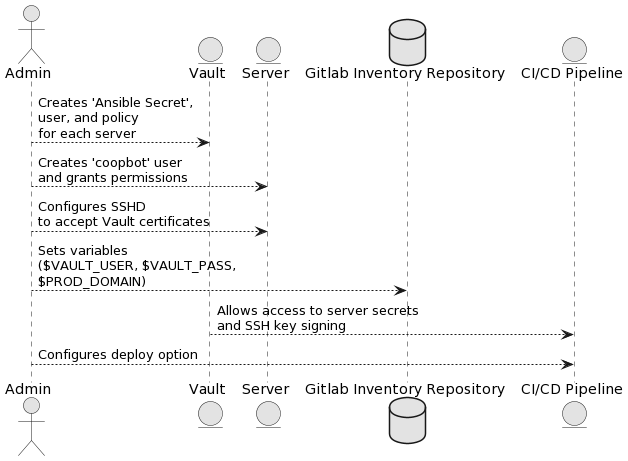
¶ Configuring brand new remote server
- Add the CA from Vault server
curl -o /etc/ssh/trusted-user-ca-keys.pem https://vault.coopdevs.org/v1/ssh-client-signer/public_key
- Configure target host to listen to keys:
# as root
echo "TrustedUserCAKeys /etc/ssh/trusted-user-ca-keys.pem" >> /etc/ssh/sshd_config.d/vault.conf
service sshd restart
- Create an user for CI
sudo useradd -m coopbot
sudo usermod -a -G sysadmin coopbot
- Give CI user required permissions to deploy
[TODO: explore which permissions are required]
¶ Run Vault Gitlab Initializer
Vault Gitlab Initializer is a CLI tool is designed to initialize instances for our CI/CD stack, integrating HashiCorp Vault and GitLab. It creates users, roles and policies in Vault, create and stores secrets, and updates environment variables in a GitLab repository based on the provided configurations.
It will:
- Create users, roles, policies and secrets in Vault
- Set enviroment variables in Gitlab
- Add a
.vault-pass.shfile to repository
¶ Configure CI
- Check that environment variables were set by
Vault Gitlab Initializerin the inventory repository:
PROD_DOMAIN=vault-test.devs.coop
VAULT_USER=citest
VAULT_SERVER_URL=https://vault.coopdevs.org
-
The
.vault-pass.shfile should be in the root of the repository. -
Edit the
gitlab-ci.ymlfile:
include:
- project: 'coopdevs/ci-cd/odoo-deploy'
file: 'deploy.yml'
# optional
file: 'badge.yml'
- Add the
auto-deploytopic to repository in Settings > General
Don’t miss this! Change CI/CD visibility are set to ‘Project Members’ in Settings > General > Visibility.
¶ Check list
## Check list for autodeployments
- [ ] Enable SSH signed keys as method in remote server.
- [ ] Create a deploy user in remote server.
- [ ] Run the `Vault Gitlab Initializer`
- [X] Create user and policy and store secret in Vault
- [X] Add CI/CD environment variables to Gitlab repository.
- [X] Created an executable `vault-pass.sh` file to retrieve the Ansible Secret
- [ ] Update `.gitlab-ci.yml` to include deploy template
- [ ] Change CI/CD visibility and set topic on repositor settings.